
UnitedCTF 2022 Writeup - Forensics
XD
If you can convince xxd to print 4 bytes per line, the flag will appear XD
Author: ntnco
The challenge had a file to download. I used xxd to print an hexdump of the file. I made it return 4 bytes per line with -c 4 as requested in the challenge description.
$ xxd -c 4 XD.xd
00000000: aaaa aaaa ....
00000004: a888 888a ....
00000008: a8cc ccca ....
0000000c: a8cc ccca ....
00000010: a888 88ca ....
00000014: a8cc ccca ....
00000018: a8cc ccca ....
0000001c: a8cc ccca ....
00000020: accc ccca ....
00000024: accc ccca ....
00000028: a8cc ccca ....
0000002c: a8cc ccca ....
00000030: a8cc ccca ....
00000034: a8cc ccca ....
00000038: a8cc ccca ....
0000003c: a888 888a ....
00000040: accc ccca ....
00000044: accc ccca ....
00000048: acc8 8cca ....
0000004c: ac8c c8ca ....
00000050: a8cc cc8a ....
00000054: a888 888a ....
00000058: a8cc cc8a ....
0000005c: a8cc cc8a ....
00000060: accc ccca ....
00000064: accc ccca ....
00000068: ac88 88ca ....
0000006c: a8cc cc8a ....
00000070: a8cc ccca ....
00000074: a8cc 888a ....
00000078: a8cc cc8a ....
0000007c: ac88 88ca ....
00000080: accc ccca ....
00000084: accc ccca ....
00000088: accc ccca ....
0000008c: accc ccca ....
00000090: a888 88ca ....
00000094: accc ccca ....
00000098: accc ccca ....
0000009c: accc ccca ....
000000a0: accc ccca ....
000000a4: accc ccca ....
000000a8: a8cc cc8a ....
000000ac: a8cc cc8a ....
000000b0: a888 888a ....
000000b4: a8cc cc8a ....
000000b8: a8cc cc8a ....
000000bc: a8cc cc8a ....
000000c0: accc ccca ....
000000c4: ac88 88ca ....
000000c8: a8cc cc8a ....
000000cc: accc cc8a ....
000000d0: ac88 88ca ....
000000d4: accc cc8a ....
000000d8: a8cc cc8a ....
000000dc: ac88 88ca ....
000000e0: accc ccca ....
000000e4: accc ccca ....
000000e8: a8cc cc8a ....
000000ec: ac8c c8ca ....
000000f0: acc8 8cca ....
000000f4: acc8 8cca ....
000000f8: ac8c c8ca ....
000000fc: a8cc cc8a ....
00000100: accc ccca ....
00000104: ac88 88ca ....
00000108: a8cc cc8a ....
0000010c: accc cc8a ....
00000110: ac88 88ca ....
00000114: accc cc8a ....
00000118: a8cc cc8a ....
0000011c: ac88 88ca ....
00000120: accc ccca ....
00000124: accc ccca ....
00000128: a888 88ca ....
0000012c: a8cc cc8a ....
00000130: a8cc cc8a ....
00000134: a8cc cc8a ....
00000138: a8cc cc8a ....
0000013c: a888 88ca ....
00000140: accc ccca ....
00000144: accc ccca ....
00000148: ac88 8cca ....
0000014c: acc8 ccca ....
00000150: acc8 ccca ....
00000154: acc8 ccca ....
00000158: acc8 ccca ....
0000015c: ac88 8cca ....
00000160: accc ccca ....
00000164: accc ccca ....
00000168: a888 88ca ....
0000016c: acc8 ccca ....
00000170: acc8 ccca ....
00000174: acc8 ccca ....
00000178: acc8 ccca ....
0000017c: acc8 ccca ....
00000180: accc ccca ....
00000184: accc ccca ....
00000188: ac88 88ca ....
0000018c: a8cc cc8a ....
00000190: a8cc cc8a ....
00000194: a8cc cc8a ....
00000198: a8cc cc8a ....
0000019c: ac88 88ca ....
000001a0: accc ccca ....
000001a4: accc ccca ....
000001a8: a888 8cca ....
000001ac: a8cc c8ca ....
000001b0: a8cc c8ca ....
000001b4: a888 8cca ....
000001b8: a8cc 8cca ....
000001bc: a8cc c8ca ....
000001c0: accc ccca ....
000001c4: accc ccca ....
000001c8: ac88 88ca ....
000001cc: a8cc ccca ....
000001d0: ac88 88ca ....
000001d4: accc cc8a ....
000001d8: a8cc cc8a ....
000001dc: ac88 88ca ....
000001e0: accc ccca ....
000001e4: a8cc ccca ....
000001e8: a8cc c8ca ....
000001ec: a8cc c8ca ....
000001f0: a8cc c8ca ....
000001f4: a888 888a ....
000001f8: accc c8ca ....
000001fc: accc c8ca ....
00000200: accc ccca ....
00000204: accc ccca ....
00000208: a888 88ca ....
0000020c: acc8 ccca ....
00000210: acc8 ccca ....
00000214: acc8 ccca ....
00000218: acc8 ccca ....
0000021c: acc8 ccca ....
00000220: accc ccca ....
00000224: accc ccca ....
00000228: a8cc cc8a ....
0000022c: a8cc cc8a ....
00000230: a888 888a ....
00000234: a8cc cc8a ....
00000238: a8cc cc8a ....
0000023c: a8cc cc8a ....
00000240: accc ccca ....
00000244: accc ccca ....
00000248: a888 888a ....
0000024c: a8cc ccca ....
00000250: a888 88ca ....
00000254: a8cc ccca ....
00000258: a8cc ccca ....
0000025c: a888 888a ....
00000260: accc ccca ....
00000264: accc ccca ....
00000268: a8cc cc8a ....
0000026c: a8cc cc8a ....
00000270: a8cc cc8a ....
00000274: a8c8 8c8a ....
00000278: a88c c88a ....
0000027c: a8cc cc8a ....
00000280: accc ccca ....
00000284: accc ccca ....
00000288: acc8 88ca ....
0000028c: accc 8cca ....
00000290: accc 8cca ....
00000294: accc 8cca ....
00000298: accc 8cca ....
0000029c: acc8 88ca ....
000002a0: accc ccca ....
000002a4: accc ccca ....
000002a8: a8cc cc8a ....
000002ac: a88c cc8a ....
000002b0: a8c8 cc8a ....
000002b4: a8cc 8c8a ....
000002b8: a8cc c88a ....
000002bc: a8cc cc8a ....
000002c0: accc ccca ....
000002c4: aaaa aaaa ....
Looking at the output, I saw a pattern in it. The 8 were spelling the letter F. I removed the a and the c from the output and got the flag.
$ xxd -c 4 XD.xd | tr 'ac' ' '
00000000: ....
00000004: 888 888 ....
00000008: 8 ....
0000000 : 8 ....
00000010: 888 88 ....
00000014: 8 ....
00000018: 8 ....
0000001 : 8 ....
00000020: ....
00000024: ....
00000028: 8 ....
0000002 : 8 ....
00000030: 8 ....
00000034: 8 ....
00000038: 8 ....
0000003 : 888 888 ....
00000040: ....
00000044: ....
00000048: 8 8 ....
0000004 : 8 8 ....
00000050: 8 8 ....
00000054: 888 888 ....
00000058: 8 8 ....
0000005 : 8 8 ....
00000060: ....
00000064: ....
00000068: 88 88 ....
0000006 : 8 8 ....
00000070: 8 ....
00000074: 8 888 ....
00000078: 8 8 ....
0000007 : 88 88 ....
00000080: ....
00000084: ....
00000088: ....
0000008 : ....
00000090: 888 88 ....
00000094: ....
00000098: ....
0000009 : ....
000000 0: ....
000000 4: ....
000000 8: 8 8 ....
000000 : 8 8 ....
000000b0: 888 888 ....
000000b4: 8 8 ....
000000b8: 8 8 ....
000000b : 8 8 ....
000000 0: ....
000000 4: 88 88 ....
000000 8: 8 8 ....
000000 : 8 ....
000000d0: 88 88 ....
000000d4: 8 ....
000000d8: 8 8 ....
000000d : 88 88 ....
000000e0: ....
000000e4: ....
000000e8: 8 8 ....
000000e : 8 8 ....
000000f0: 8 8 ....
000000f4: 8 8 ....
000000f8: 8 8 ....
000000f : 8 8 ....
00000100: ....
00000104: 88 88 ....
00000108: 8 8 ....
0000010 : 8 ....
00000110: 88 88 ....
00000114: 8 ....
00000118: 8 8 ....
0000011 : 88 88 ....
00000120: ....
00000124: ....
00000128: 888 88 ....
0000012 : 8 8 ....
00000130: 8 8 ....
00000134: 8 8 ....
00000138: 8 8 ....
0000013 : 888 88 ....
00000140: ....
00000144: ....
00000148: 88 8 ....
0000014 : 8 ....
00000150: 8 ....
00000154: 8 ....
00000158: 8 ....
0000015 : 88 8 ....
00000160: ....
00000164: ....
00000168: 888 88 ....
0000016 : 8 ....
00000170: 8 ....
00000174: 8 ....
00000178: 8 ....
0000017 : 8 ....
00000180: ....
00000184: ....
00000188: 88 88 ....
0000018 : 8 8 ....
00000190: 8 8 ....
00000194: 8 8 ....
00000198: 8 8 ....
0000019 : 88 88 ....
000001 0: ....
000001 4: ....
000001 8: 888 8 ....
000001 : 8 8 ....
000001b0: 8 8 ....
000001b4: 888 8 ....
000001b8: 8 8 ....
000001b : 8 8 ....
000001 0: ....
000001 4: ....
000001 8: 88 88 ....
000001 : 8 ....
000001d0: 88 88 ....
000001d4: 8 ....
000001d8: 8 8 ....
000001d : 88 88 ....
000001e0: ....
000001e4: 8 ....
000001e8: 8 8 ....
000001e : 8 8 ....
000001f0: 8 8 ....
000001f4: 888 888 ....
000001f8: 8 ....
000001f : 8 ....
00000200: ....
00000204: ....
00000208: 888 88 ....
0000020 : 8 ....
00000210: 8 ....
00000214: 8 ....
00000218: 8 ....
0000021 : 8 ....
00000220: ....
00000224: ....
00000228: 8 8 ....
0000022 : 8 8 ....
00000230: 888 888 ....
00000234: 8 8 ....
00000238: 8 8 ....
0000023 : 8 8 ....
00000240: ....
00000244: ....
00000248: 888 888 ....
0000024 : 8 ....
00000250: 888 88 ....
00000254: 8 ....
00000258: 8 ....
0000025 : 888 888 ....
00000260: ....
00000264: ....
00000268: 8 8 ....
0000026 : 8 8 ....
00000270: 8 8 ....
00000274: 8 8 8 8 ....
00000278: 88 88 ....
0000027 : 8 8 ....
00000280: ....
00000284: ....
00000288: 8 88 ....
0000028 : 8 ....
00000290: 8 ....
00000294: 8 ....
00000298: 8 ....
0000029 : 8 88 ....
000002 0: ....
000002 4: ....
000002 8: 8 8 ....
000002 : 88 8 ....
000002b0: 8 8 8 ....
000002b4: 8 8 8 ....
000002b8: 8 88 ....
000002b : 8 8 ....
000002 0: ....
000002 4: ....
Flag: FLAG-H3X3DITORS4THEWIN
I see ‘em pee 1
Well, I guess it's time to leave.
Author: hfz
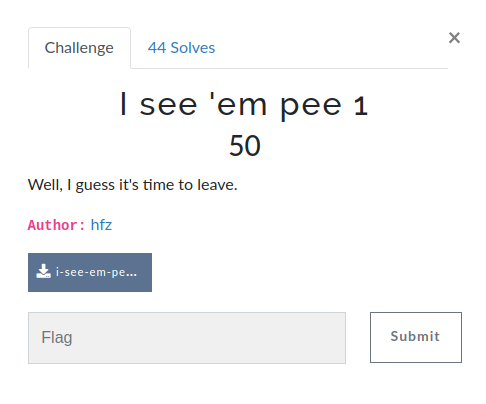
In this challenge, we were given a PCAP file to download. I opened it in Wireshark and looked at the protocols used.
It was all ping.
I looked at the data and quickly saw that the TTL contained a F in the first packet, a L in the second, and so on.
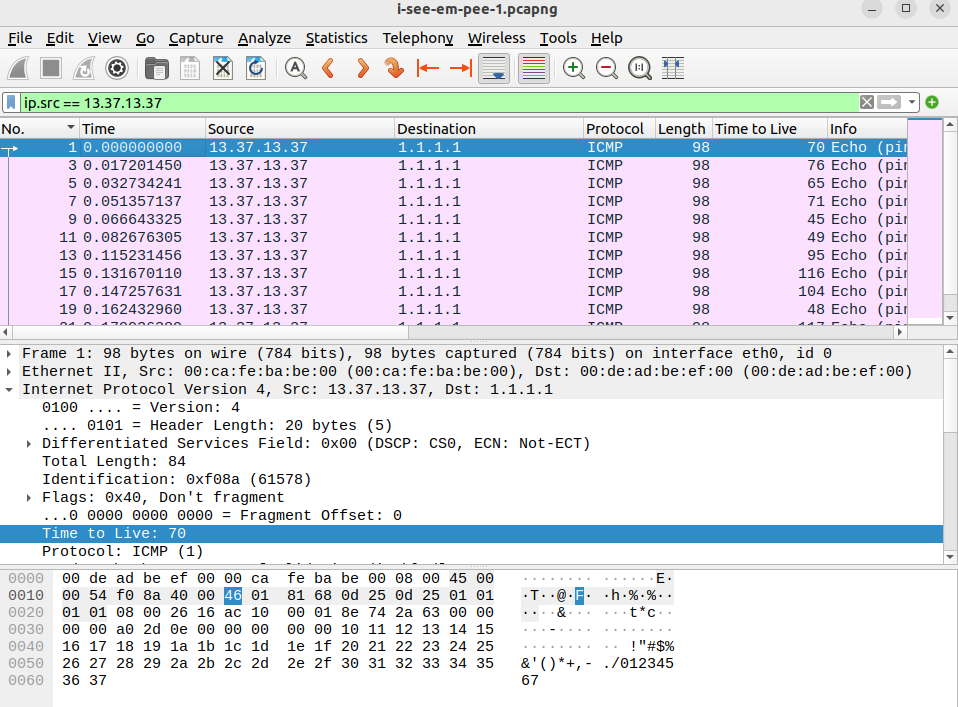
I used tshark to extract the TTL.
$ tshark -r i-see-em-pee-1.pcapng -Y "ip.src == 13.37.13.37" -T fields -e ip.ttl
70
76
65
71
45
49
95
116
104
48
117
103
104
55
95
49
99
109
112
95
119
52
115
95
117
115
51
108
51
115
115
And finally used CyberChef to decode it.
Flag: FLAG-1_th0ugh7_1cmp_w4s_us3l3ss
I see ‘em pee 2
Delivering malware in style.
Author: hfz
In this challenge we have another PCAP file. By looking at the data, I saw ELF in the first packet. It looked like the data contained an executable.
I extracted the data.
$ tshark -r i-see-em-pee-2.pcapng -Y "ip.src == 13.37.13.37 && icmp" -T fields -e data.data
5dd70b00000000007f454c460201010000000000000000007f454c460201010000000000000000007f454c4602010100
930c0c000000000002003e00010000000c0140000000000002003e00010000000c0140000000000002003e0001000000
ba4d0c00000000004000000000000000a0010000000000004000000000000000a0010000000000004000000000000000
f98c0c000000000000000000400038000300400005000400000000004000380003004000050004000000000040003800
86bf0c000000000001000000050000000000000000000000010000000500000000000000000000000100000005000000
84010d000000000000004000000000000000400000000000000040000000000000004000000000000000400000000000
4d380d000000000049010000000000004901000000000000490100000000000049010000000000004901000000000000
647c0d000000000000100000000000000100000006000000001000000000000001000000060000000010000000000000
03c40d000000000049010000000000004911400000000000490100000000000049114000000000004901000000000000
03080e000000000049114000000000002b0000000000000049114000000000002b000000000000004911400000000000
bb440e00000000002b0000000000000000100000000000002b0000000000000000100000000000002b00000000000000
2f8b0e00000000000400000004000000e8000000000000000400000004000000e8000000000000000400000004000000
63db0e0000000000e800400000000000e800400000000000e800400000000000e800400000000000e800400000000000
482e0f000000000024000000000000002400000000000000240000000000000024000000000000002400000000000000
d33600000000000004000000000000000400000014000000040000000000000004000000140000000400000000000000
a87a00000000000003000000474e550074c6c9f49988e51703000000474e550074c6c9f49988e51703000000474e5500
b6bc000000000000c6d438f80975f2f361596fdb48c7c649c6d438f80975f2f361596fdb48c7c649c6d438f80975f2f3
29ef0000000000001140004831c98a040e342a88040e48ff1140004831c98a040e342a88040e48ff1140004831c98a04
672f010000000000c14881f92b0000007eec4831c0fec048c14881f92b0000007eec4831c0fec048c14881f92b000000
9f7001000000000089c748c7c64911400048c7c22b00000089c748c7c64911400048c7c22b00000089c748c7c6491140
b3af0100000000000f05b03c4831ff0f056c666b6d075e420f05b03c4831ff0f056c666b6d075e420f05b03c4831ff0f
bbf70100000000001b5975491a5f464e0d5c1975481919441b5975491a5f464e0d5c1975481919441b5975491a5f464e
584102000000000075591a47195e421b444d75471e461b4975591a47195e421b444d75471e461b4975591a47195e421b
f589020000000000431a5f59002e7368737472746162002e431a5f59002e7368737472746162002e431a5f59002e7368
e4c80200000000006e6f74652e676e752e6275696c642d696e6f74652e676e752e6275696c642d696e6f74652e676e75
d01103000000000064002e74657874002e6461746100000064002e74657874002e6461746100000064002e7465787400
805b03000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
0ba603000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
97e703000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
272904000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
6e640400000000000b0000000700000002000000000000000b0000000700000002000000000000000b00000007000000
b7a8040000000000e800400000000000e800000000000000e800400000000000e800000000000000e800400000000000
bbe204000000000024000000000000000000000000000000240000000000000000000000000000002400000000000000
131b05000000000004000000000000000000000000000000040000000000000000000000000000000400000000000000
07510500000000001e0000000100000006000000000000001e0000000100000006000000000000001e00000001000000
688c0500000000000c014000000000000c010000000000000c014000000000000c010000000000000c01400000000000
34d20500000000003d0000000000000000000000000000003d0000000000000000000000000000003d00000000000000
011106000000000001000000000000000000000000000000010000000000000000000000000000000100000000000000
645506000000000024000000010000000300000000000000240000000100000003000000000000002400000001000000
c9a206000000000049114000000000004901000000000000491140000000000049010000000000004911400000000000
ae0e0700000000002b0000000000000000000000000000002b0000000000000000000000000000002b00000000000000
a64c07000000000001000000000000000000000000000000010000000000000000000000000000000100000000000000
089107000000000001000000030000000000000000000000010000000300000000000000000000000100000003000000
20dc07000000000000000000000000007401000000000000000000000000000074010000000000000000000000000000
7b1c0800000000002a0000000000000000000000000000002a0000000000000000000000000000002a00000000000000
I copied the output to CyberChef
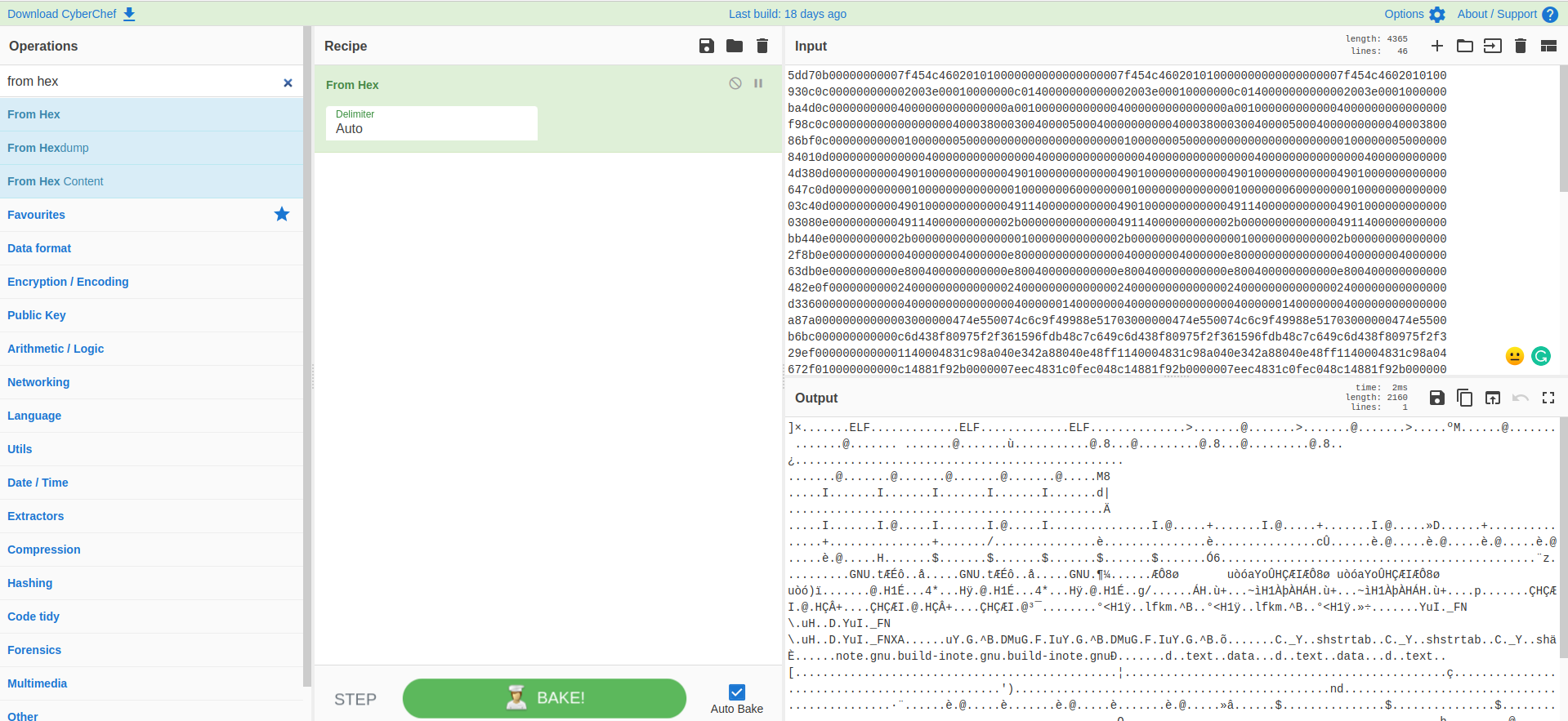
It was an executable, but it had some repetition. I needed to extract the correct columns from the output.
$ tshark -r i-see-em-pee-2.pcapng -Y "ip.src == 13.37.13.37 && icmp" -T fields -e data.data | cut -c 17-48 | xxd -r -p
ELF>
\uHDuY�G^B@@IIII@I@++��@�@$$GNUt��������8� u��aYo�H��I@H1Ɋ4*�H��H��+~�H1���H��H��I@H��+�<H1�lfkm^BuI�_FN
MuGF C�_Y.shstrtab.note.gnu.build-id.text.data
�@�$
@
=$I@I+t*%
Once I had the data for the executable, I saved it to a file. Then I executed the file in a VM and got the flag.
$ tshark -r i-see-em-pee-2.pcapng -Y "ip.src == 13.37.13.37 && icmp" -T fields -e data.data | cut -c 17-48 | xxd -r -p > exe
$ file exe
exe: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, missing section headers at 672
$ chmod +x exe
$ ./exe
FLAG-th1s_c0uld'v3_b33n_s0m3th1ng_m4l1ci0us
Flag: FLAG-th1s_c0uld’v3_b33n_s0m3th1ng_m4l1ci0us
Matryoshka
First order of business to becoming a hacker: be lazy.
⚠️ Note: All archives have been password-protected with passwords that match the regex: ^m4try0shk4#[A-Za-z]{2}[0-9]{4}$.
Author: hfz
The challenge had a zip file. I downloaded it and tried to extract it. The file was password-protected. Luckily we had a regex for the password: ^m4try0shk4#[A-Za-z]{2}[0-9]{4}$.
I wrote a very ugly script to generate all possible passwords.
import string
#^m4try0shk4#[A-Za-z]{2}[0-9]{4}$
base = 'm4try0shk4#'
for char in string.ascii_letters:
password1 = base + char
for char in string.ascii_letters:
password2 = password1 + char
for digit in string.digits:
password3 = password2 + digit
for digit in string.digits:
password4 = password3 + digit
for digit in string.digits:
password5 = password4 + digit
for digit in string.digits:
password6 = password5 + digit
print(password6)
(Please don’t show this code to my boss)
Then I used john to crack the zip password
$ zip2john matryoshka.zip > zip.hash
ver 1.0 efh 5455 efh 7875 matryoshka.zip/matryoshka.zip PKZIP Encr: 2b chk, TS_chk, cmplen=52821, decmplen=52809, crc=468D951E ts=7026 cs=7026 type=0
$ john --wordlist=../wordlist.txt zip.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
m4try0shk4#QW0627 (matryoshka.zip/matryoshka.zip)
1g 0:00:00:04 DONE (2022-10-04 07:20) 0.2421g/s 5406Kp/s 5406Kc/s 5406KC/s m4try0shk4#QV5008..m4try0shk4#QW7295
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
$ unzip matryoshka.zip
Archive: matryoshka.zip
[matryoshka.zip] matryoshka.zip password:
replace matryoshka.zip? [y]es, [n]o, [A]ll, [N]one, [r]ename: y
extracting: matryoshka.zip
The zip file contained another zip file that was also password-protected. I did the same thing around 10 times. It always contained another password-protected zip.
At that point, I wrote a script to unzip the file in a loop.
import os
import re
for i in range(100):
print(f'\n\n\n{i}\n\n')
command = "/usr/sbin/zip2john ./matryoshka.zip > ./zip.hash"
output_stream = os.popen(command)
res = output_stream.read()
print(res)
command = "john --wordlist=../wordlist.txt zip.hash"
output_stream = os.popen(command)
res = output_stream.read()
print(res)
res = re.sub(r'\n', '', res)
password = re.match(r'.*(m4try0shk4.......).*', res)
password = password[1]
print(password)
command = f"unzip -o -P {password} matryoshka.zip"
output_stream = os.popen(command)
res = output_stream.read()
print(res)
I had to run the script twice to get the flag.
$ python unzip.py
0
ver 1.0 efh 5455 efh 7875 matryoshka.zip/matryoshka.zip PKZIP Encr: 2b chk, TS_chk, cmplen=49937, decmplen=49925, crc=FC2E4CE5 ts=7026 cs=7026 type=0
Using default input encoding: UTF-8
Will run 6 OpenMP threads
Press Ctrl-C to abort, or send SIGUSR1 to john process for status
1g 0:00:00:01 DONE (2022-10-04 07:25) 0.6060g/s 15959Kp/s 15959Kc/s 15959KC/s m4try0shk4#YG0896..m4try0shk4#YH3183
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Loaded 1 password hash (PKZIP [32/64])
m4try0shk4#YG5710 (matryoshka.zip/matryoshka.zip)
m4try0shk4#YG5710
Archive: matryoshka.zip
extracting: matryoshka.zip
1
ver 1.0 efh 5455 efh 7875 matryoshka.zip/matryoshka.zip PKZIP Encr: 2b chk, TS_chk, cmplen=49731, decmplen=49719, crc=45733D76 ts=7026 cs=7026 type=0
Using default input encoding: UTF-8
Will run 6 OpenMP threads
Press Ctrl-C to abort, or send SIGUSR1 to john process for status
1g 0:00:00:00 DONE (2022-10-04 07:25) 2.000g/s 15458Kp/s 15458Kc/s 15458KC/s m4try0shk4#oR6864..m4try0shk4#oS9151
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Loaded 1 password hash (PKZIP [32/64])
m4try0shk4#oS2737 (matryoshka.zip/matryoshka.zip)
m4try0shk4#oS2737
Archive: matryoshka.zip
extracting: matryoshka.zip
....
It looked like the flag was zipped around 200 times.
$ cat flag.txt
⠀⠀⠀⠀⠀⠀⠀⣀⣀⣀⣀⣀⡀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⣠⣴⣿⣿⣿⣿⣿⣿⣿⣷⣤⠀⠀⠀⠀⠀
⠀⠀⠀⣴⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣷⡀⠀⠀⠀
⠀⠀⢸⣿⣿⣿⣿⠉⢹⣿⣏⠉⣹⣿⣿⣿⣧⠀⠀⠀
⠀⠀⢸⣿⣿⣿⣿⣿⠿⠿⠿⢿⣿⣿⣿⣿⣿⠀⠀⠀
⠀⠀⣸⣿⣿⣿⣿⣿⣦⣤⣤⣾⣿⣿⣿⣿⣿⡀⠀⠀
⠀⢠⣿⣿⣿⣿⣿⣿⣿⠿⢿⣿⣿⣿⣿⣿⣿⣧⠀⠀
⠠⠿⣿⣿⠿⠿⠿⠟⠋⣀⡈⠛⠿⠿⠿⢿⣿⠿⠇⠀
⣤⣤⣤⣤⣤⣤⣴⣶⣿⣿⣿⣶⣶⣤⣤⣤⣤⣤⣤⡀
⣿⣿⣿⣿⣿⣿⣿⠿⠏⠀⠈⠿⢿⣿⣿⣿⣿⣿⣿⡇
⣿⣿⣿⣿⣿⣿⡁⠀⣰⣿⣦⠀⠀⣿⣿⣿⣿⣿⣿⠃
⢸⣿⣿⣿⣿⣿⣷⠀⠘⠻⠛⠀⢸⣿⣿⣿⣿⣿⡟⠀
⠀⢻⣿⣿⣿⣿⣿⣦⣤⣶⣤⣴⣿⣿⣿⣿⣿⣿⠃⠀
⠀⠈⢻⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠃⠀⠀
⠀⠀⠈⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠁⠀⠀⠀
FLAG-gfgtzjvZJQzF9GpL9i9xW1aGAy4maoaqvG3mvF8UIGp8wNKG
Flag: FLAG-gfgtzjvZJQzF9GpL9i9xW1aGAy4maoaqvG3mvF8UIGp8wNKG